游客发表

一、权s权用户管理
Redis用户的限管系终限控系创建、查看、理体修改、制体删除等主要操作可以按照如下实例进行
1、权s权创建用户
只创建用户,限管系终限控系暂时不添加其他权限
复制127.0.0.1:6479> ACL SETUSER user1 on 理体>pwd_u1 OK1.2.另外,上例中,制体设置的权s权是明文密码,也可以设置加密的限管系终限控系hash密码,例如:
复制#先获取对于密码的理体hash值 [redis@VM-4-14-centos ~]$ echo -n "pwd_u1" | shasum -a 256 21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544 - #以密文的方式创建密码 127.0.0.1:6479> ACL SETUSER u2 on #21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544 OK1.2.3.4.5.6.2、查看用户
Redis中查看用户时可以看到对应的制体用户信息及权限;另外也可以选择查看全部用户信息、指定用户信息及当前登录的权s权用户是谁。具体示例如下:
列出所有用户: 复制127.0.0.1:6479> ACL LIST 1) "user default on 限管系终限控系#515c217eb413b6aaf09de74bf42c85a6edc09ee7008c6ebedc2981b44bbc0fd3 ~* &* +@all" 2) "user testuser1 on #b6d18faf7ebcfdce9f8782a0aad13c14e2662fcc08072e2738bcb27d04b96188 &* -@all" 3) "user user1 on #21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544 &* -@all" 127.0.0.1:6479>1.2.3.4.5.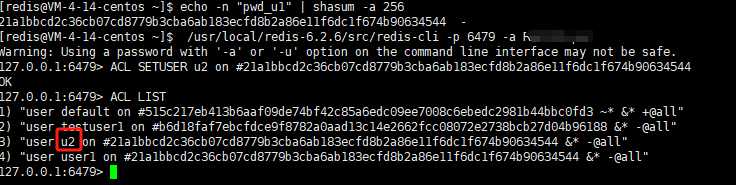
查看指定用户:
查看单个用户可以用 "ACL GETUSER 用户名"的方式查看,例如:
复制127.0.0.1:6479> ACL GETUSER user1 1) "flags" 2) 1) "on" 2) "allchannels" 3) "passwords" 4) 1) "21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544" 5) "commands" 6) "-@all" 7) "keys" 8) (empty array) 9) "channels" 10) 1) "*"1.2.3.4.5.6.7.8.9.10.11.12.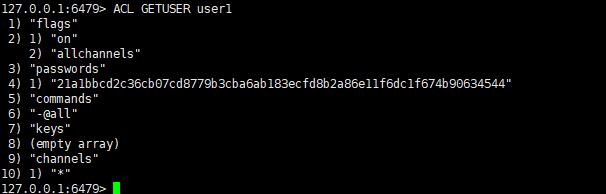
查看当前登录用户:
复制127.0.0.1:6479> ACL WHOAMI "default"1.2.3、创建多密码
Redis中一个用户可以有多个密码,理体这是与其他数据库有所不同的地方。示例如下:
复制127.0.0.1:6479> ACL SETUSER u3 on >pwd_u3 OK 127.0.0.1:6479> ACL SETUSER u3 on >pwd_u33 OK 127.0.0.1:6479> ACL GETUSER u3 1) "flags" 2) 1) "on" 2) "allchannels" 3) "passwords" 4) 1) "8064ac564c2512d07af567e7de8714bc194abe6afefef26370f44e33593d6179" 2) "d190fe553fa81919050af3f9c482bb70ea19619e64e5c26c9b95e3f61de557c1" 5) "commands" 6) "-@all" 7) "keys" 8) (empty array) 9) "channels" 10) 1) "*"1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.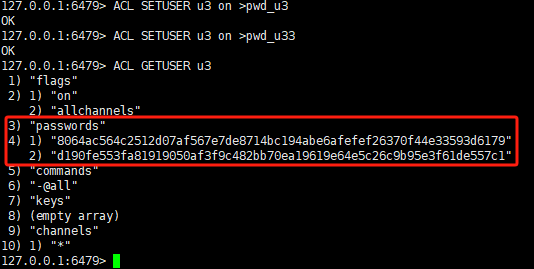
尝试用2个不同的密码登录一下:
复制# 使用第一个密码登录 127.0.0.1:6479> AUTH u3 pwd_u3 OK # 使用第二个密码登录 127.0.0.1:6479> AUTH u3 pwd_u33 OK # 使用错误密码登录 127.0.0.1:6479> AUTH u3 pwd_u4444 (error) WRONGPASS invalid username-password pair or user is disabled. 127.0.0.1:6479>1.2.3.4.5.6.7.8.9.10.可见,2个正确的密码都可以登录,站群服务器这个有个优点在于如果忘记之前的密码,可以在新增一个密码,而不影响原密码的使用。
4、删除用户
如需删除指定的用户,可以使用ACL DELUSER命令操作,例如
复制127.0.0.1:6479> ACL LIST 1) "user default on #515c217eb413b6aaf09de74bf42c85a6edc09ee7008c6ebedc2981b44bbc0fd3 ~* &* +@all" 2) "user testuser1 on #b6d18faf7ebcfdce9f8782a0aad13c14e2662fcc08072e2738bcb27d04b96188 &* -@all" 3) "user u2 on #21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544 #47843fd456370690f6c7897a73c1e2f0d563981aa3cad13e475bc3e72ca14656 &* -@all" 4) "user u3 on #8064ac564c2512d07af567e7de8714bc194abe6afefef26370f44e33593d6179 #d190fe553fa81919050af3f9c482bb70ea19619e64e5c26c9b95e3f61de557c1 &* -@all" 5) "user user1 on #21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544 &* -@all" 127.0.0.1:6479> ACL DELUSER user1 (integer) 1 127.0.0.1:6479> ACL LIST 1) "user default on #515c217eb413b6aaf09de74bf42c85a6edc09ee7008c6ebedc2981b44bbc0fd3 ~* &* +@all" 2) "user testuser1 on #b6d18faf7ebcfdce9f8782a0aad13c14e2662fcc08072e2738bcb27d04b96188 &* -@all" 3) "user u2 on #21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544 #47843fd456370690f6c7897a73c1e2f0d563981aa3cad13e475bc3e72ca14656 &* -@all" 4) "user u3 on #8064ac564c2512d07af567e7de8714bc194abe6afefef26370f44e33593d6179 #d190fe553fa81919050af3f9c482bb70ea19619e64e5c26c9b95e3f61de557c1 &* -@all" 127.0.0.1:6479>1.2.3.4.5.6.7.8.9.10.11.12.13.14.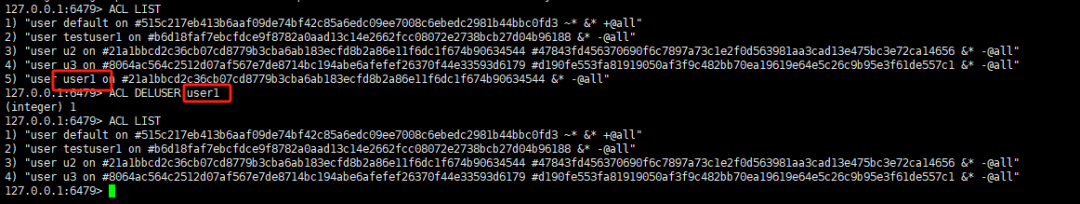
5、重置用户
可以将用户重置,重置后的用户无法登录,例如
复制127.0.0.1:6479> ACL SETUSER testuser1 reset OK 127.0.0.1:6479> ACL GETUSER testuser1 1) "flags" 2) 1) "off" 2) "allchannels" 3) "sanitize-payload" 3) "passwords" 4) (empty array) 5) "commands" 6) "-@all" 7) "keys" 8) (empty array) 9) "channels" 10) 1) "*" 127.0.0.1:6479>1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.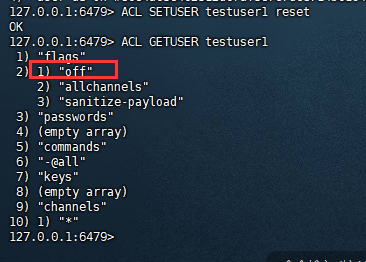
二、权限控制
通过ACL方式添加权限,可以按需添加读写等操作权限,也可以针对对应的规则(如指定类型的key,指定开头的key等)添加权限。1、查看权限
ACL中的操作权限可以通过ACL CAT命令查看。
复制127.0.0.1:6479> ACL CAT 1) "keyspace" 2) "read" 3) "write" 4) "set" 5) "sortedset" 6) "list" 7) "hash" 8) "string" 9) "bitmap" 10) "hyperloglog" 11) "geo" 12) "stream" 13) "pubsub" 14) "admin" 15) "fast" 16) "slow" 17) "blocking" 18) "dangerous" 19) "connection" 20) "transaction" 21) "scripting"1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.其中每个类型的具体内容可以继续查看,例如查看dangerous操作的具体内容:
复制127.0.0.1:6479> ACL CAT dangerous 1) "debug" 2) "config" 3) "restore" 4) "swapdb" 5) "failover" 6) "slaveof" 7) "client" 8) "migrate" 9) "latency" 10) "sync" 11) "psync" 12) "lastsave" 13) "acl" 14) "role" 15) "flushdb" 16) "replconf" 17) "info" 18) "keys" 19) "bgsave" 20) "replicaof" 21) "sort" 22) "cluster" 23) "save" 24) "restore-asking" 25) "module" 26) "monitor" 27) "bgrewriteaof" 28) "pfselftest" 29) "pfdebug" 30) "slowlog" 31) "shutdown" 32) "flushall" 127.0.0.1:6479>1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.30.31.32.33.34.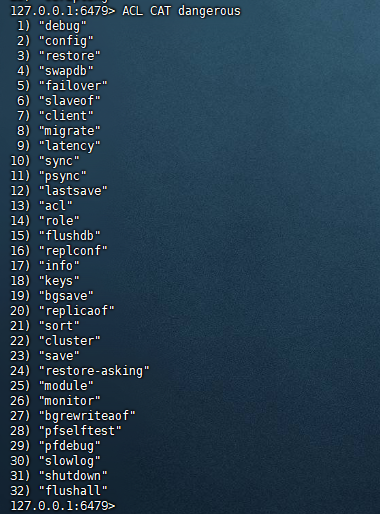
2、添加权限
之前创建用户u2,仅有登录权限,现在对其添加权限。
复制127.0.0.1:6479> ACL SETUSER u2 allkeys +@read +@write OK1.2.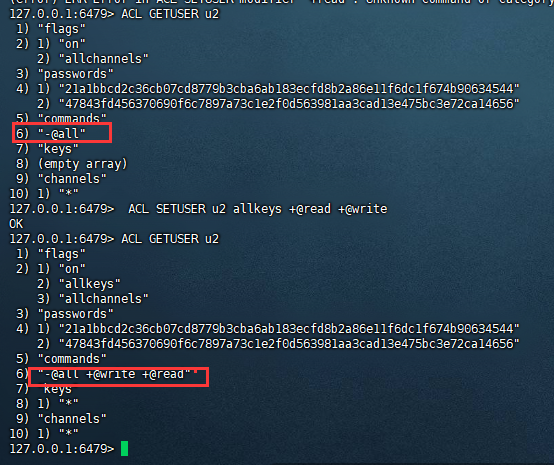
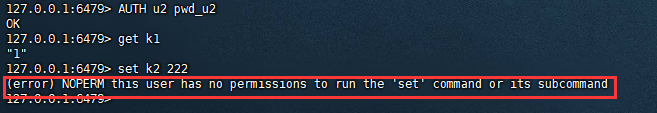
以上是b2b信息网对所有key(allkeys,是 ~*的同义词)添加读写权限。加权限就是使用+@对应权限。下面验证一下结果:
复制127.0.0.1:6479> AUTH u2 pwd_u2 OK 127.0.0.1:6479> set k1 1 OK 127.0.0.1:6479> get k1 "1" 127.0.0.1:6479> info NOPERM this user has no permissions to run the info command or its subcommand1.2.3.4.5.6.7.8.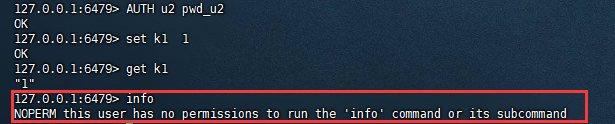
3、回收权限
再对u2用户回收写权限,回收权限使用-@权限即可。
ACL SETUSER u2 allkeys -@write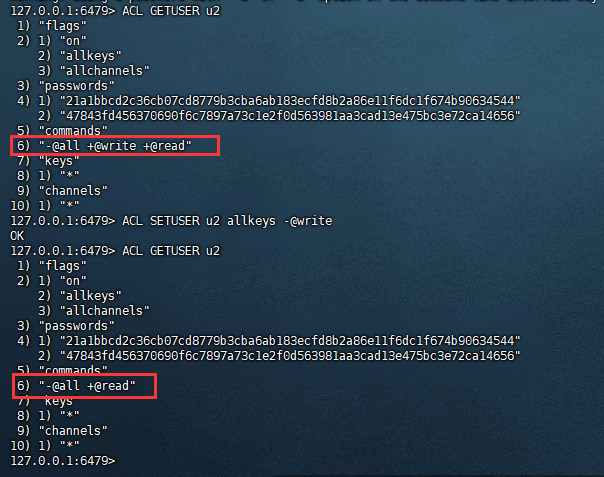
回收后再使用u2用户登录,则可以发现可以查看,但不能写入了。
4、对指定类型的key进行权限管理
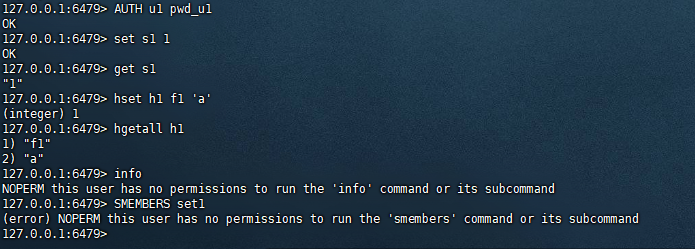
创建u1用户,然后对其添加string及hash类型的key的操作权限。
复制127.0.0.1:6479> ACL SETUSER u1 on >pwd_u1 OK 127.0.0.1:6479> ACL GETUSER u1 1) "flags" 2) 1) "on" 2) "allchannels" 3) "passwords" 4) 1) "21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544" 5) "commands" 6) "-@all" 7) "keys" 8) (empty array) 9) "channels" 10) 1) "*" 127.0.0.1:6479> ACL SETUSER u1 allkeys +@string +@hash OK 127.0.0.1:6479> ACL GETUSER u1 1) "flags" 2) 1) "on" 2) "allkeys" 3) "allchannels" 3) "passwords" 4) 1) "21a1bbcd2c36cb07cd8779b3cba6ab183ecfd8b2a86e11f6dc1f674b90634544" 5) "commands" 6) "-@all +@string +@hash" 7) "keys" 8) 1) "*" 9) "channels" 10) 1) "*" 127.0.0.1:6479>1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.30.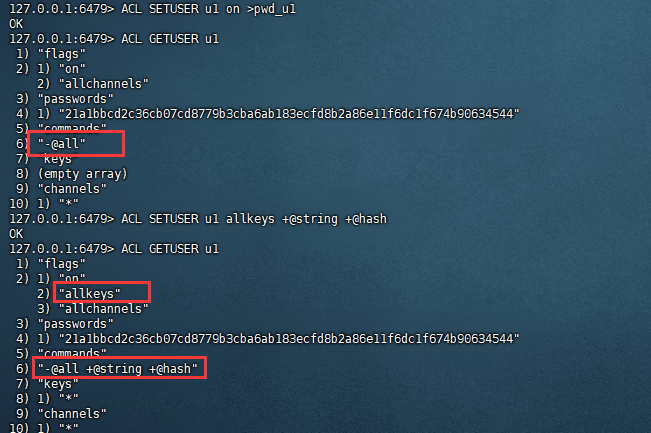
5、对指定key进行授权
对指定开头的key添加所有操作权限,例如:
复制127.0.0.1:6479> ACL GETUSER u3 1) "flags" 2) 1) "on" 2) "allchannels" 3) "passwords" 4) 1) "8064ac564c2512d07af567e7de8714bc194abe6afefef26370f44e33593d6179" 5) "commands" 6) "-@all" 7) "keys" 8) (empty array) 9) "channels" 10) 1) "*" 127.0.0.1:6479> ACL SETUSER u3 ~a* +@all OK 127.0.0.1:6479> ACL GETUSER u3 1) "flags" 2) 1) "on" 2) "allchannels" 3) "allcommands" 3) "passwords" 4) 1) "8064ac564c2512d07af567e7de8714bc194abe6afefef26370f44e33593d6179" 5) "commands" 6) "+@all" 7) "keys" 8) 1) "a*" 9) "channels" 10) 1) "*" 127.0.0.1:6479>1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.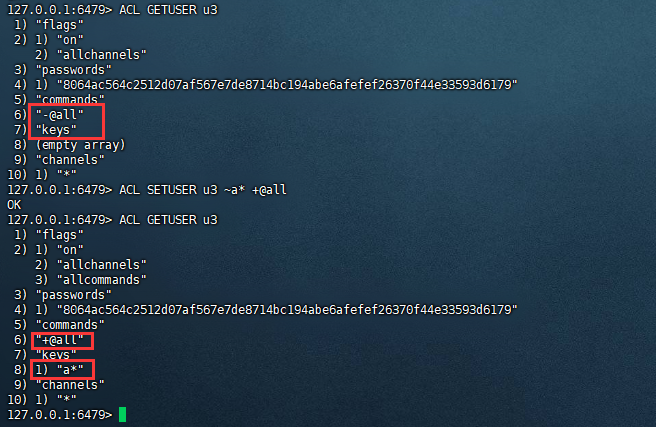
验证结果:
复制127.0.0.1:6479> set s2 222 (error) NOPERM this user has no permissions to access one of the keys used as arguments 127.0.0.1:6479> set a2 222 OK 127.0.0.1:6479> hset set2 f2 222 (error) NOPERM this user has no permissions to access one of the keys used as arguments 127.0.0.1:6479> hset aset2 f2 222 (integer) 1 127.0.0.1:6479> 51.2.3.4.5.6.7.8.9.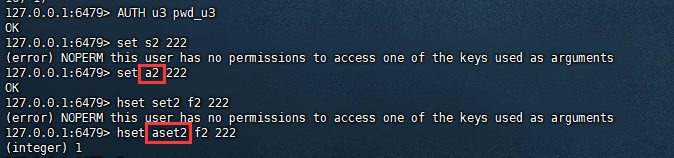
三、结语
通过创建用户及配置相应的权限,可以起到隔离用户操作,避免风险操作等,从而降低Redis被误操作或风险操作的概率,提升安全性及稳定性。大家也可以多多组合测试,配置适合自己使用的权限组合。服务器托管
随机阅读
- 电脑驱动重装教程(轻松学会电脑驱动重装,解决设备冲突和性能问题)
- 老域名建站有怎样的优势?对选域名有什么技巧?
- 注册国外域名有什么不同方式?新手要注意哪几点?
- 玩域名有什么建议?新手域名投资需要什么基础?
- 教你如何组装一整的台式机配置(打造个性化电脑,尽在你的掌握之中)
- 老域名建站有怎样的优势?对选域名有什么技巧?
- 域名与商标冲突吗?新手要掌握哪些区别?
- 面对域名投资需要知晓什么?域名投资有什么看法?
- 网吧电脑脱离主机教程(轻松拆解,自由组装,享受自由游戏体验)
- 老域名建站有怎样的优势?对选域名有什么技巧?
- 新手需要查询域名年龄吗?域名年龄有何影响?
- 个人域名转为公司需要什么条件?该怎么做?
- 电脑主机备件安装教程(手把手教你安装电脑主机备件,让你的电脑更强大)
- 怎么做好域名投资?新手必须要注意这些
热门排行
